Prime cyber insurance for growth by optimising caps, capacity and capital

To develop the next generation of cyber insurance – as a widely available, widely affordable mass-market product – carriers will need to solve long-standing structural problems first. We’ve identified three levers for achieving this:
Mitigate individual risks through enhanced cybersecurity
Rightsize exposure, especially for cyber catastrophes
Expand access to capital for cyber underwriters
We covered the first of these – risk mitigation through enhanced cybersecurity – previously. Today we shift from individual risks to risk portfolios, exploring the other two levers: rightsizing of exposures and expansion of underwriting capital.
Currently, cyber can bring very large losses, both through blown-out limits and catastrophic events enveloping many policyholders simultaneously. But if they can cap losses and optimise overall capacity – rightsizing exposure, so to speak – insurers can dampen this dynamic. This will in turn expand access to the capital the line needs and lastingly bring down market prices.
Cap claim costs through decisive incident response
Decisive early action as cyber catastrophes are unfolding – just as with natural catastrophes – can help curtail large individual losses. So, how do insurers facilitate this?
First and foremost through efficient pay-out, funds can be immediately put to work on containment. Some innovators like Parametrix and Qomplx even bring the parametric model to cyber, sidestepping the claims/adjustment process entirely to provide “bridging” liquidity well in advance of traditional processes being completed.
Moreover, insurers (and brokers) should integrate dedicated incident response services into their offering – giving clients access to a specialist advice as soon as an incident is detected.
Since many clients already pay for incident response independently of any insurance, there is an alternative model insurers may consider.
Rather than piping security offerings into insurance policies, they could instead pipe insurance into a security offering. As discussed previously, cybersecurity and cyber insurance could be integrated cost-effectively within a managed-security layer – and managed Detection and Response (MDR), or Security Operations Centre as a Service (SOCaaS), would be natural extensions to this and create further synergies.
Click/tap to view a larger image.
In 2022, the global SOCaaS market sits at ~$450m but will approach $700m by 2025, driven by demand for specialist services in cyber forensics, regulatory compliance and crisis communications.
Right-size cyber exposure through smart capacity allocations
Any initiative to cap cyber claims is welcome. However, large individual losses aren’t the only troublesome dynamic at play in the line.
Earlier, we characterised cyber as an “unnatural catastrophe” – capable of wreaking the same devastation across an insurer’s book as a hurricane or earthquake but seemingly less straightforward to diversify.
However, it’s easy to overstate the diversification problem in cyber.
A useful touchstone is found in recent discussions about the insurability of pandemics. With Covid-19, governments showed their power to shutter entire sectors and markets overnight – potentially triggering Business Interruption (BI) claims from every policyholder on the book. If Covid-19 represents the limit case for diversification, where does cyber sit by comparison? Some way short, certainly.
Indeed, while cyber risk may not share the seasonal rhythms of NatCat, this doesn’t mean there are no rhythms that carriers can adapt to balance their portfolios.
For a start, cybercrime is really its own economy, in which hackers pivot opportunistically between multiple attack avenues – meaning not all cyber classes are necessarily correlated. A few years ago, the favoured cyberattack was the data breach, but breaches have since receded in the face of a vast ransomware bubble. Now, in a further twist, we see instances of “double extortion” combining ransoms with leaks.
Long-term data on the mechanics of the “cyber economy” remains limited – and making this useful for insurance is a further bridge yet. However, it will surely benefit underwriters to break cyber out into its constituent perils – each as different from the next as flooding, earthquake and wildfire within NatCat. Each one brings a different loss profile, with implications for pricing, diversification, exclusions and sub-limits.
Actuary vs. Hacktuary: facing up to the ransomware challenge
Ransomware is much discussed in the context of exclusions and sub-limits. To contrast the case of data breaches: loss here is proportional to breach size (e.g. number of customers affected), meaning that safe limits can be set based on maximum breach size. Cyber ransoms meanwhile can be arbitrarily high. So, safe limits on policies set up to cover data breaches are rapidly maxed out by ransoms – if ransomware is added to the policy without further thought.
Obviously, it’s possible to adapt policies for ransomware – with higher premiums and more capital. However, the cover is already expensive and capital already constrained. With such limits on the risk the industry can assume, a small reduction in ransomware exposure potentially goes a long way towards expanding other coverage types and customer volumes as the industry strives for stable returns.
A further challenge is hackers’ scope for smarter pricing, as “hacktuaries” seek the sweet spot for setting ransoms. Especially as ransomware cover becomes more widespread, average ransom demands may creep towards limits, necessitating higher premiums and higher limits still – a vicious circle that serves only to fund hackers.
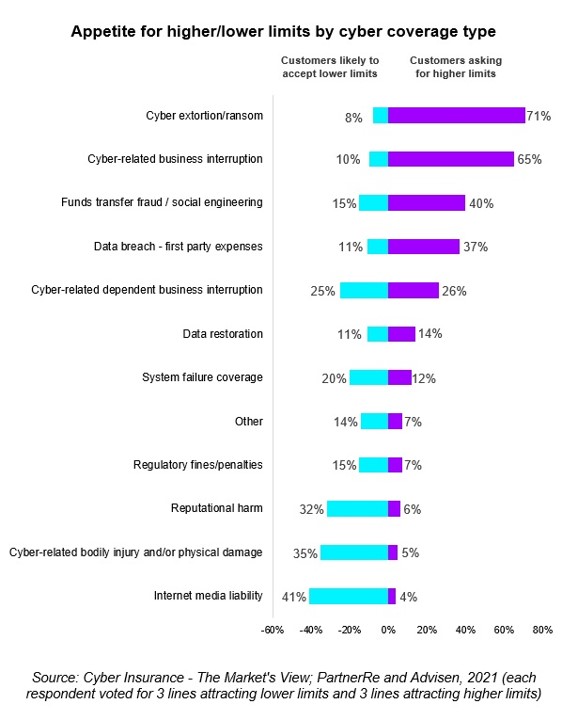
In response, some insurers have gone as far as to suspend ransomware payments. However, any drive to fully exclude ransomware will likely meet resistance from policyholders: in a recent survey of cyber underwriters and brokers, cover for “cyber extortion/ransom” saw the greatest appetite for higher limits and lowest appetite for limit reduction.
 Click/tap to view a larger image.
Click/tap to view a larger image.
Unpick cyber aggregations through AI-driven portfolio analysis
Ultimately, there are no quick fixes to cyber’s diversification problem. Even if you can play with the balance of cyber classes you hold, risks within each class will remain strongly correlated.
For instance, successful ransomware attacks are always likely to hit a high percentage of policyholders due to the ease with which hackers can copy and paste the same attack template. However, in time, attack replicability could decline as firms’ operating and security environments become increasingly customised – meaning that risks within the same class, like ransomware, will eventually de-aggregate.
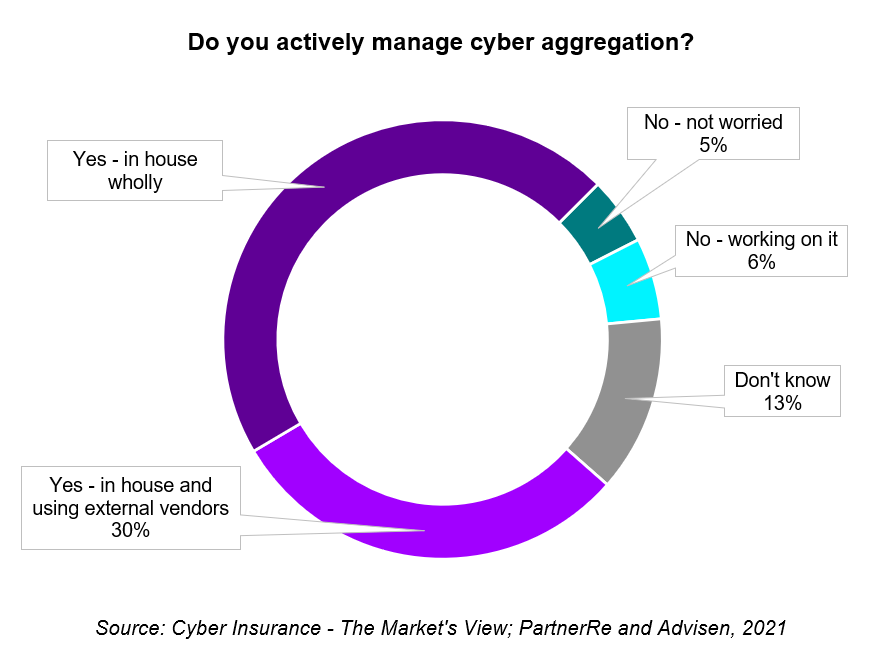
Much of this is speculative, so substantial portfolio analysis – likely AI-driven – will be required to really understand where aggregations are occurring and which factors are genuinely useful for achieving better diversification. Currently, around three-quarters of cyber underwriters actively manage cyber aggregations:
 Click/tap to view a larger image.
Click/tap to view a larger image.
Time will bring greater adoption and sophistication of portfolio analysis – as well as its tighter integration into risk selection and pricing. This way, insurers can optimise capacity allocation, reduce the cost of capital and, with it, bring down prices for end customers.
We began this series by observing that cyber insurance as we know it is broken – with high prices throttling scale and improvements in the line. The portfolio-level interventions described here – separation of individual cyber perils plus data-driven approaches to diversification – will do much to “unbreak” the line, especially if combined with enhanced cybersecurity to mitigate individual risks. This brings us to the final piece of the puzzle: underwriting capital.
If you build it, underwriting capital will come
At the heart of the cyber hard market is a dearth of capital for writing cyber risk – representing a final limit on market growth. So, how will this be resolved?
The bad news is that there’s no quick fix for growing capacity: for as long as cyber risk is seen as a speculative investment, underwriters will struggle to grow its capital base. As with any prospect, the sector must prove it is truly investment-grade; only then will capital providers move cyber into the bread-and-butter portion of their portfolios, with the larger and more regular allocations that brings.
The good news is that cyber will not remain a speculative investment indefinitely.
Everything we’ve discussed in this series – best-practice cybersecurity, rapid incident response, limits to catastrophic exposures, aggregation management – takes us closer to a product that can deliver stable returns at scale. As with a jigsaw, solve the rest and the last piece slots in by itself; fix cyber underwriting and capital will duly flow in.
Capital will come from many quarters. Existing cyber (re)insurers, having “cracked” the line, will write more business. Similarly, carriers that currently wait on the wings – those with limited appetite for speculation, we might say – will feel better able to make their debut.
Given the potentially vast quantity of cyber risks waiting to be written, alternative capital will likely play a role in meeting future demand. Transactions involving insurance-linked securities (ILS) have so far been rare in cyber, largely reflecting the speculative nature of the risk. However, plenty of things recommend cyber risks to outside investors in the longer term:
Given low-interest rates, cyber offers yield – decoupled from the wider money markets and potentially existing Cat investments also
While traditional Cat risks can trap investor capital over many years as claims develop, cyber is shorter-tailed – letting investors move in and out with relative ease
The hard-market returns on offer today will continue to spur financial invention. In the years ahead, we may even see Cyber Cat Bonds – assuming the market can develop acceptable ways to rate them. Meanwhile, sidecar-like structures are already being experimented with by a handful of major carriers.
Shorter-term, carriers must take a pragmatic approach to scale the line. It’s not merely about milking today’s hard conditions; nor is it about going for broke solving all the world’s cyber problems. By pulling the levers discussed here, insurers can build a functioning cyber market from the ground up: growing the number of customers with some cyber protection, scaling up sub-lines and, eventually, arriving at a suite of mass-market products.
We hope you’ve enjoyed this series – for more info, download our cyber insurance report. To further discuss any of the ideas we’ve covered, please get in touch.
Get the latest insurance industry insights, news, and research delivered straight to your inbox.
Disclaimer: This content is provided for general information purposes and is not intended to be used in place of consultation with our professional advisors.







